Let's describe stream of authentication request for Basic HTTP Authentication utilized in MVC application. At first, customer sends HTTP request to get some aid situated at URL. This request has no authentication credentials of any sort, so it can be anonymous, random call.
As the request has no credentials, Spring filters will move it by with none uncommon processing. Security configuration determines whether it really is allowed or not and what exact roles authenticated consumer will need to need to entry the aid . In our case we assume that the aid requires consumer to be authenticated, so AbstractSecurityInterceptor will throw some subclass of AuthenticationException. This exception shall be caught by ExceptionTranslationFilter which is one among many filters within the default safety chain. ExceptionTranslationFilter will validate style of the exception and if it certainly is AuthenticationException it really is going to delegate name to AuthenticationEntryPoint component.
For Basic Authentication, it can put together right HTTP Response with so referred to as 'Authentication Challenge', which can be standing 401 and suitable headers for Basic. Browsers screen a dialog for the consumer to enter username and password, different valued clientele can do various issues to acquire such credentials. Before we start off additional configuration we've to elucidate one attention-grabbing influence of our work. Standard username is "user" and the password will probably be generated each time when our software is constructed and proven on terminal. If that is your first time with Spring Security, you are able to carry out a number of tests, create only REST API and ship the request on this endpoint.
You will get response with 401 standing and Unauthorized error. If you add user/user and password/generated password (key/value) headers the Spring Security must authorize you and will let you get entry to this endpoint. We could configure default consumer in application.properties file including spring.security.user.name and spring.security.user.password parameters.
Both ID and entry tokens are fetched from the OIDC supplier as a half of the authorization code flow. ID token is usually verified on each consumer request because the first token which is used to symbolize the principal and extract the roles. Access token just isn't verified by default because it can be supposed to be propagated to the downstream services. The verification of the entry token ought to be enabled whether it can be injected as a JWT token. To keep customers from reusing a deleted cookie, we advise that you simply configure as brief an expiration time for the entry token as is reasonable. The result's the same, a different request for a similar resource, however with credentials in suitable HTTP Headers.
First, they extract credentials and use them to construct Authentication object that acts as enter for additional processing. This Authentication is exceeded to AuthenticationManager that asks its configured and hooked up AuthenticationProviders, if any of them can course of such variety of Authentication . By default, there's such issuer for Basic and it'll question UserDetailsService for UserDetails object corresponding for such username. This UserDetails will then be validated towards password and if the whole lot is present, matches and is in any different case correct, new output Authentication object will probably be created. This output object is marked as efficiently authenticated and crammed with GrantedAuthorities that corresponds to the roles assigned to this exact user.
For that end-user interplay to happen, you will have to create a Single-Page Application register with Auth0. Please take a look at an easy controller class which explains behaviors of our safety implementations. Before, we needed to add 2 customers to our database with admin and consumer roles. Please recall to make use of password encoder in the course of a consumer create. In this article, we construct an Ionic app that talks to a Spring Boot again end.
After a victorious login, the consumer app receives a JWT from the server and shops it in localStorage. Next time the consumer opens the app, the appliance reads the JWT from localStorage and sends it within the request header to the server. When the token remains to be valid, the consumer is instantly logged in. At the identical time it grants enormous configuration options. And the large potentialities of any implementation of ordinary authentication and authorization course of mechanisms makes it a particularly preferred and sometimes used framework. In addition, JWT lets you ship your authorization signature securely with no applying a delicate information.
Next step will join our database and switch the created consumer to the spring safety context. Let's create a UserDetailsServiceImpl class which implements a UserDetailsService interface. It's a practical interface since it has just one approach to override so we could use a lambda expression.
This methodology returns any class which implements a UserDetail interface and can current us our consumer in a safety context. We return a fundamental User class from Spring Security package. Additionally, if quarkus.oidc.token.issuer property is configured then it is going to likely be used as an OidcConfigurationMetadata issuer property value. If this property is enabled then a refresh token request might be carried out if the ID token has expired and, if successful, the nearby session might be up to date with the brand new set of tokens.
Otherwise, the neighborhood session shall be invalidated and the consumer redirected to the OpenID Provider to re-authenticate. In this case the consumer is probably not challenged once more if the OIDC supplier session remains to be active. For this feature be valuable the authentication.session-age-extension property additionally needs to be set to a non-zero worth because the refresh token is presently stored within the consumer session.
This possibility is legitimate solely when the appliance is of kind ApplicationType#WEB_APP. Now, let's get returned to our WebSecurityConfig class and finish the remainder of our configuration. If we remember, we're going to require our AuthenticationManager bean for our Jwt controller class and add the filter we simply created to our configuration. We are additionally going to configure which requests are to be authenticated and which aren't to be. We shall additionally add the AuthenticationEntryPoint to our requests to ship returned the 401 error response.
Since, we additionally don't should take care of session variables when applying jwt we could make our session STATELESS. The procedure right here extracts the token from the header and validates it with the assistance of validateJwtToken() approach to our TokenManager class. During validation, it checks for the username and the expiration date. If equally the values are valid, we save the authentication in our Spring Security context and let the code proceed to the subsequent filter in our filter chain. ManagementEndpointAuthenticationFilter is a twin of AuthenticationFilter however it surely doesn't make use of tokens.
It has hardcoded backend admin login username with password presented from property at deployment time. It checks if username and password from headers matches these when concentrating on Spring-Actuator endpoints that require authentication. Each time a request is shipped to the server, it could wish to be authenticated in order that the appliance can be certain that the request is from a legitimate consumer and determine the user. The simplest method to do that is by sending the username and password with every request.
Theoretically, one might create some type of session and retailer this data in a cookie. But periods are tough to keep up when the appliance grows with numerous customers and in addition in circumstances the place there's one than extra backend server. Spring Security gives you a safety service for our spring application. Hopefully, this submit may additionally assist in seeing the great image of this sub-framework.
The code must use the identical secret key as within the generate way to be able to ascertain the validity of the token. It then extracts the subject, which is the username in our application, and reads the consumer from the "database". Instead of doing a database query, you possibly can keep all facts into the JWT and extract them here. Doing a database question right right here has the improvement that we will at once block a consumer or change his roles, however additionally poses a bottleneck when you have got hundreds and hundreds of users.
If the consumer logs out, the refresh fails and the load balancer redirects the consumer to the IdP authorization endpoint. This allows the load balancer to drop periods after the consumer logs out. Now that we included what these authentication techniques are, let's begin implementing them. What we're going to do is about up a Spring Boot software to have a database of customers with encoded passwords.
Then, we're going to configure HTTP essential authentication for each request. In this filter class extendingOncePerRequestFilterabstract class, we'll implement thedoFilterInternalmethod for you to filter all of the incoming requests. We get the JWT token from the Authorisation header and validate it.
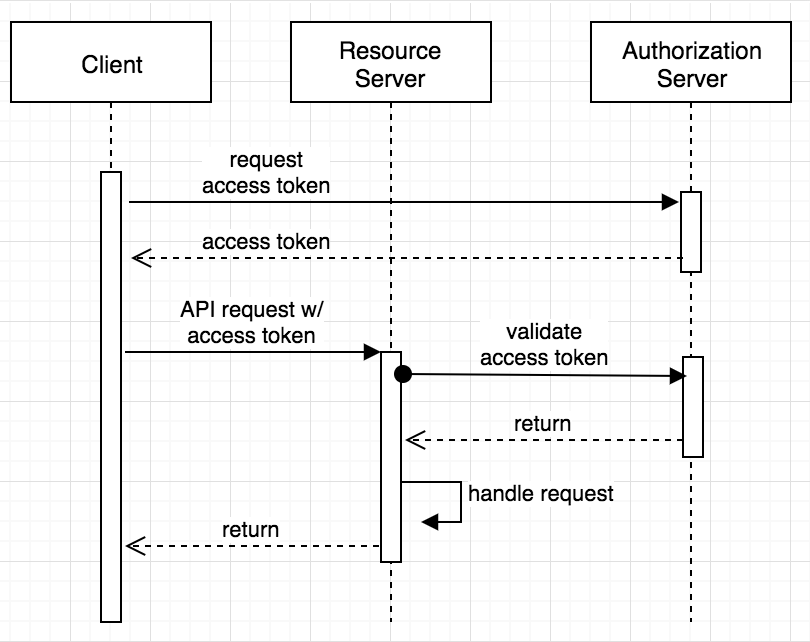
Then we get the consumer particulars fromUserDetailsServiceand populate authentication in safety context. OAuth encapsulates entry data in an entry token. In turn, OpenID Connect encapsulates id data in an ID token. The authentication server can ship these two tokens to the shopper software initiating the process. When the consumer requests a protected API endpoint, it should ship the entry token together with the request.
If name is just not for authenticating endpoint, we test even if we've token in header. If there's a token, we transfer to a different processing path. In some different case, we move name additional to the dispatcher. While we might quickly return 401 with no chaining we might lose all effective tune safety config – we would like our name to proceed and be processed by dispatcher regulations and/or methodology rules. There can be some companies that don't require authentication or a name can be for some static useful resource like icon. Nonetheless, any safety violation will finish in spring AuthenticationException to be thrown, caught by ExceptionTranslationFilter and our unathorizedEntryPoint called.
We have an curiosity in checking our customers within the database so we now must add Spring Data JPA and MySQL Driver for quick entry to our database. The added dependencies want a database configuration, I favor to add it in a properties file. We have to add spring.datasource.url, spring.datasource.username, spring.datasource.password properties. In the past section, we arrange an authentication course of and configured public/private URLs. This could be sufficient for straightforward applications, however for many real-world use cases, we normally want role-based entry insurance policies for our users.
In this chapter, we'll handle this situation and arrange a role-based authorization schema making use of the Spring Security framework. The name to /authenticate is debatable, because the question to fetch the consumer from the database. On the opposite hand, we're sending a further request to the server, which may be a bottleneck in case you've gotten hundreds of users. To authenticate a user, a buyer software ought to ship a JSON Web Token within the authorization header of the HTTP request to your backend API.
API Gateway validates the token on behalf of your API, so that you don't should add any code in your API to course of the authentication. The use of JWT token for authorization is essentially the most typical of its applications. The token will likely be generated within the server and despatched to the customer the place it's saved within the session storage or neighborhood storage. To entry a protected aid the customer would ship the JWT within the header as given above.
We will see the JWT implementation in Spring Security within the part below. The login(…) way will intercept the POST requests to the endpoint /user and obtain the consumer and password as parameters. As you may see, no consumer and password validation is carried out on this example, so we enable any worth of those parameters to cross through. Obviously, for an actual project, at this level we might authenticate the consumer towards our database or any exterior provider. In WebSecurityConfig.java, we'll modify default spring safety measures by extending WebSecurityConfigurerAdapter class.
Here we'll outline our HTTP request filter and a default response when the consumer is unauthenticated. Once the demo software masses again, click on on the Menu tab. In this mode, the demo buyer allows you to entry UI components that make requests to your API write endpoints as an unauthenticated visitor.
If your API safety is working correctly, it could reject these requests. It one way or the other tries to authenticate by some supplier certain mechanism after which create Authentication implementation referred to as AuthenticatedExternalWebService. This implementation additionally holds a Stub or Proxy to genuine exterior internet service. This Stub/Proxy will use authenticated calls, possibly over the network. This authenticated service can maintain any safety context like WS-Security, Basic credentials, OAuth2 Bearer Token etc.
AuthenticationFilter will then set this AuthenticatedExternalWebService in TokenService and later retrieve it when validating token and put into SecurityContextHolder. The "supports" way tells Spring's AuthenticationManager what class of enter Authentication this supplier is competent to processing. Authenticate way tries to authenticate consumer by username and password. It validates parameters presence and delegates to implementation of an actual supplier coming from exterior service. It is a spot through which you'll ask database, service, reminiscence or another facility. This occasion is handed to Spring's AuthenticationManager, which finds AuthenticationProvider that helps one of these enter Authentication.
We count on returned output Authentication occasion to not be null and be authenticated. It's a very good follow to maintain Authentication implementations immutable, notwithstanding I'm not entirely conforming to this rule . It, then, straight away returns http response with OK and JSON with generated token. No different filter down the chain known as so no controller way is executed.
It can be enhanced to cross the request to AuthenticationController and to permit it to return the token and 200 OK Status, however I simply desired to illustrate a point. To grant required authentication and authorization amenities you want to both create them from the scratch or use present safety framework. Writing such a framework from the scratch is nearly by no means a very good idea. It's elaborate and must be completely tested, ideally hardened on the battlefield of production. Better thought is to make use of some existing, matured and confirmed frameworks. The pure selection for Springers is to make use of Spring-Security.
Formerly often called Acegi Security, later included beneath the umbrella of Spring components, Spring-Security is only a jar file that you simply contain within the program improvement project. It promises you with huge quantity of well-designed performance able to be utilized to your application. It is a framework that promises you numerous however on the opposite facet it continues to be tremendously complicated, mainly, because of tremendously so much of working components and universal nature of safety associated mechanisms.






















No comments:
Post a Comment
Note: Only a member of this blog may post a comment.